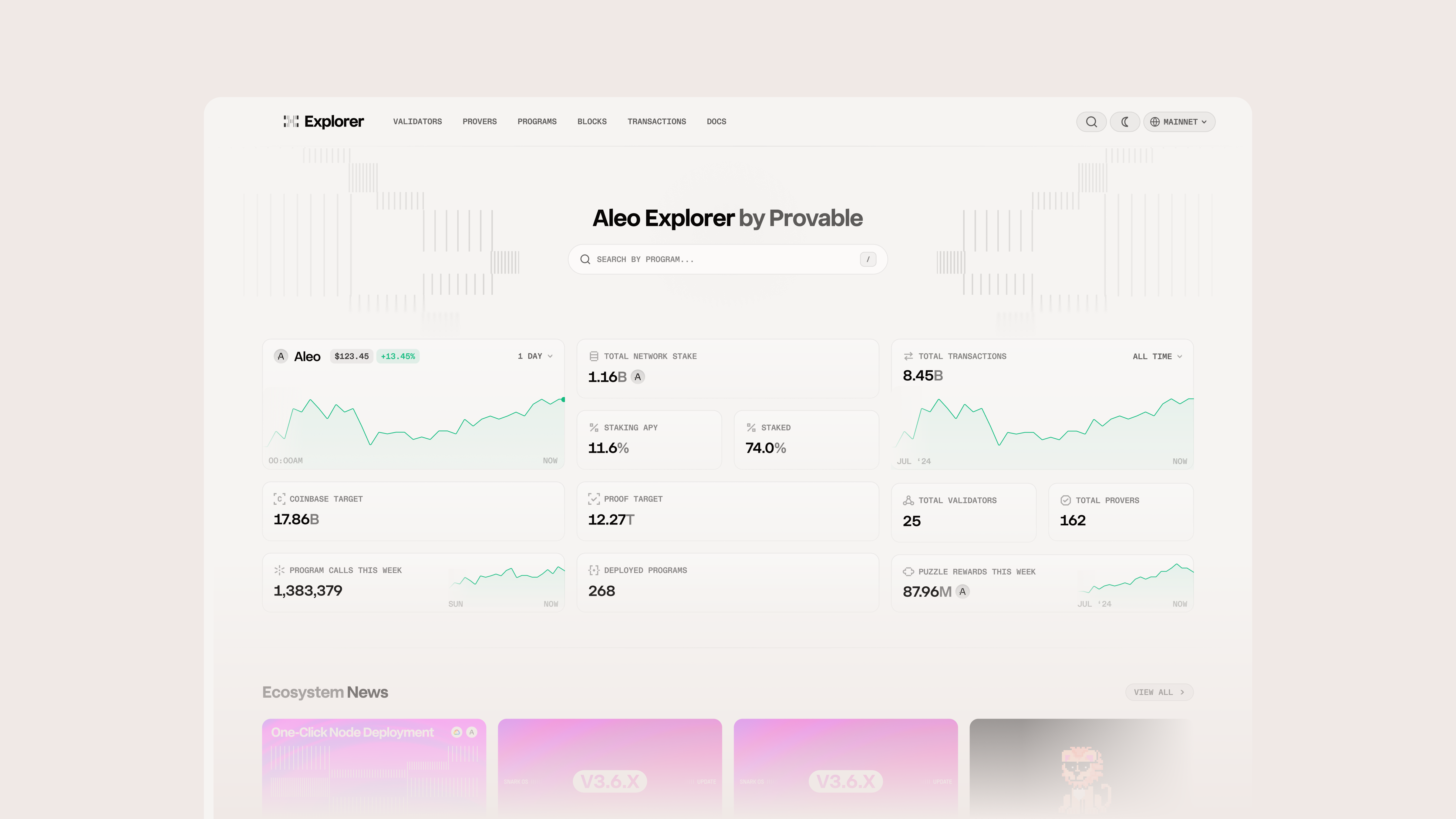
Explorethe AleoNetwork
DeFi TVL
 Pondo$2,542,480.05
Pondo$2,542,480.05 Verulink$2,465,947.9
Verulink$2,465,947.9 Beta Staking$1,613,514.87
Beta Staking$1,613,514.87 Arcane Finance$242,278
Arcane Finance$242,278 AlphaSwap$70.12
AlphaSwap$70.12

Want to build cryptographically secure dApps at scale?
Use the Provable SDK to build secure, private applications on Aleo. Empowering digital privacy.
Learn more